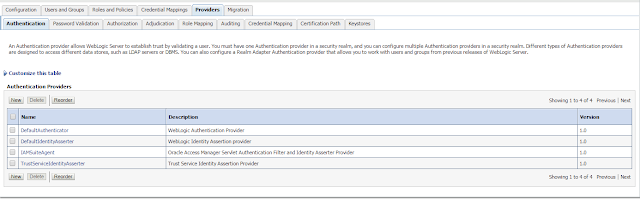
Architecture:
It’s the same way to do. Read this article for details
Here, I determine the difference between them.
Configure OHS
[obiee@ptudvtg142 ohs1]$ pwd
/home/obiee/middleware/Oracle_WT1/instances/instance1/config/OHS/ohs1
[obiee@ptudvtg142 ohs1]$ more
mod_wl_ohs.conf
# NOTE : This is a template to configure mod_weblogic.
LoadModule weblogic_module
"${ORACLE_HOME}/ohs/modules/mod_wl_ohs.so"
# This empty block is needed to save mod_wl related configuration from
EM to this file when changes are made at the Base Virtual Host Level
<fModule weblogic_module>
# WebLogicHost
# WebLogicPort
# Debug ON
# WLLogFile
/tmp/weblogic.log
# MatchExpression *.jsp
</IfModule>
# <Location /weblogic>
# SetHandler
weblogic-handler
# PathTrim /weblogic
# ErrorPage http:/WEBLOGIC_HOME:WEBLOGIC_PORT/
# </Location>
<Location /xmlpserver>
SetHandler weblogic-handler
WebLogicHost 192.168.2.142
WebLogicPort 9704
</Location>
<Location /analytics>
SetHandler weblogic-handler
WebLogicHost 192.168.2.142
WebLogicPort 9704
</Location>
|
Configure BI Publisher for SSO
Step 1: Login BI Publisher as administrator
Choose Administration à
Security Center à
Security Configuration
Step 2: On Authentication
area, Tick Use Single Sign-On
Single Sign-on Type: Oracle
Access Manager
Single Sign-Off URL: http://192.168.2.149:14102/oam/server/logout
How to get username: HTTP
Header
User Name Parameter: OAM_REMOTE_USER
How to get user locale: HTTP
Parameter
User Locale Parameter LOCALE_LANGUAGE
Click Apply.
Step 3: Reboot Weblogic Server (AdminServer) and Managed Server (bi_server1)
Test Single Sign-On:
Step 1: Login to BI Publisher via OHS
Step 2: Redirect to OAM login Form
Step 3: Enter username and password and click Login
Step 4: Login Successful